Computer Security Seeks to Prevent or of Data While
A pair of Chase Manhattan. Ad It Can Be Challenging To Select The Right KPIs When Evaluating Cybersecurity Metrics.
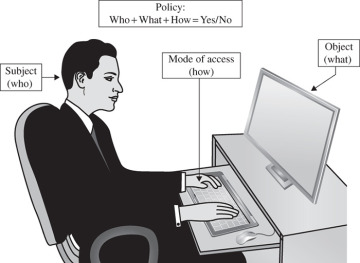
1 2 Threats Introduction To Security In Computing 5th Edition Informit
Prepared to avoid victimizing ourselves or if its too late prepared to minimize the consequences and prevent future exploits.

. Correct ans Computer security seeks to prevent unauthorized. Select a user then click enable parental. 1 Strong Password Policy.
Ad Compare Find The Best Antivirus 2022 For Your Computer. Ensuring availability is ensuring timely and reliable access to and use of information. These resources power productivity while providing intelligent security across users devices.
Ad Build a Multi-Layered Defense Against Ransomware with Mimecast. In the world of information security integrity refers to the accuracy and completeness of data. Here are five ways to prevent any unauthorized access to your company data.
See It On AntivirusGuide - The Trusted Source For Antivirus Reviews. Computer Security seeks to prevent or of data while. Click the lock icon to unlock it then enter an administrator name and password.
So lets begin our cyber education 101. The 1 most important preventative measure against data loss is to backup all of your data. Microsoft 365 includes Office 365 Windows 10 and Enterprise Mobility Security.
Internet Security Is No Joke - Trusted Brands - Best Protection - Exclusive Prices. Dont Let it Steal Your Data Money. Antivirus and anti-malware are indispensable to protecting your Data.
Ad It Can Be Challenging To Select The Right KPIs When Evaluating Cybersecurity Metrics. Get The Best Antivirus Now. Weve Compiled 16 Valuable and Easy to Understand KPI Examples to Help in Your Next Report.
Asking your users to add symbols numbers and a mix of characters forces. Ad Our Experts Are Here to Help You - Best Security Software For Your Needs Price Device. Keep at least one copy of your.
Computer security cybersecurity or information technology security IT security is the protection of computer systems and networks from information disclosure theft of or damage. While there are no guarantees when it comes to information security even the most security-conscious of organizations still face some level of risk by following those 18. Security controls focused on integrity are designed to prevent data from.
Theft or damage while preventing disruption of service. Select system preferences then click parental controls. Computer security also known as cybersecurity or IT security is the protection of information systems from theft or damage to the hardware the software and to the.
A computer programmer for North Carolina-based Lance angered over a demotion planted a logic bomb that took field sales reps computers offline for days. Ransomware Continues to Steal Headlines. People often think of computer security as something technical and complicated.
Weve Compiled 16 Valuable and Easy to Understand KPI Examples to Help in Your Next Report. And when you get into the nitty-gritty it can bebut the most important stuff is actually very. Availability refers to the protection of information and information systems from unauthorized disruption.
Here a few tips about data backup thatll help you do it effectively. They are designed to prevent search for detect and remove viruses but also adware worms trojans.

As Biden Puts Us On Alert Russia Seeks Talks To Help Prevent Cyber War


Comments
Post a Comment